Phan Duong Hieu and Neal Koblitz Original article published in Cryptologia magazine, Volumn 41, Issue 6.
Our friends…admired the determination and sacrifice coming from a small nation standing up against a colossal empire… Our narrative was like the Biblical story of David against Goliath.— Nguyễn Thị Bình (Family, Friends and Country, p 141-142)
P2: Cryptography during the French and American wars in Vietnam (Part 2)
1. Introduction
Does the history of cryptography during the French and American wars in Vietnam have any relevance to the concerns of people working in information security in the 21st century? The years 1945–1975 predate public key cryptography, predate DES, and hugely predate the internet. Nevertheless, there are several reasons why this story needs to be told in our time.
In the first place, the victories — shocking and unexpected to many in the West — of a technologically backward people over two advanced industrialized Western countries were signature events of the 20th century. The humiliation of the French at Điện Biên Phủ in the spring of 1954 marked the beginning of the end of French colonialism; it was an inspiration to others, mainly in northern Africa, who were suffering under the yoke of French colonialism and who managed to achieve independence a few years later. Similarly, the expulsion of American forces from southern Vietnam on 30 April 1975 — which was the only time the United States has ever been decisively defeated in a war — gave tremendous encouragement to others, especially in Latin America, who were struggling against U.S. hegemony.
Given this analysis, one might think that if we looked at the technological side of warfare — and, in particular, at communications intelligence — we would find that the Việt Minh (the name of the front that fought for independence from the French), the National Liberation Front (NLF), and the Democratic Republic of Vietnam (DRVN) must have been consistently outmatched and outclassed by French and American expertise and equipment. However, the truth of the matter is much more complex. During both the French and American wars, as we shall see, there was a surprising symmetry between the adversaries in both signals intelligence (SIGINT) and communications security (COMSEC). There were dramatic successes and major failures on all sides.
Perhaps the lesson to be drawn is that in SIGINT and COMSEC during the colonial wars in Indochina the human element was primary, and the technical element was secondary. Is this any less true of today’s applications of cryptography? Indeed, if one can extract a single short message from Ross Anderson’s thousand-page classic Security Engineering (Anderson 2008), it is that the human factor is just as central to cybersecurity in the internet age as it was to communications security during the wars of earlier times.
2. The French War (1945–1954) and the Inter-War Period (1954–1960)
2.1 The early years
From the beginning the leadership in Hanoi attached great importance to communications intelligence. According to a history by the Vietnamese government that was translated by the NSA (NSA 2014), the People’s Armed Forces cryptographic branch was formed on 12 September 1945, just ten days after the Declaration of Independence of Vietnam. At that time the cryptographic level of the Vietnamese was not high. As described in the Cryptographic Bureau’s history (Ban Cơ Yếu n.d.), the system they were using in late 1945 and early 1946 was little more than a Caesar cipher. More precisely, they would first regard the Vietnamese text as letters in a largely Latin alphabet, that is, drop the accents and merge some letters such as a, â, ă (which are distinct letters in Vietnamese). Then they would number the letters and shift the numbers by a fixed amount (in the illustrative example (Ban Cơ Yếu n.d.) the Caesar key is 10). The sequence of decimal numbers would be the ciphertext.
Then on 10 April 1946, the department heads were ordered to use a better, though still rudimentary, double encryption system. First, they would encode the different letters and accents using combinations of Latin letters; for example, “Lê Thái” would become LEETHAIS. Then they would convert to numbers using a fixed random permutation of the numbers 0 through 22 (three letters of the Latin alphabet were not used). Finally, they would encrypt the decimal digits with a Vigenère key of length 5 (that is, a 5-digit decimal number). The message digits would be divided into blocks of length 5, and the key would be added digit by digit modulo 10.
This system is very weak in comparison with state-of-the-art cryptography in 1946 and also in comparison with the systems used by the Vietnamese during the American war. The second layer of encryption can easily be stripped away; it compares unfavorably to ordinary Vigenère encryption with a 5-letter key, for which key recovery through frequency analysis would require one to examine a fair amount of ciphertext. In the first place, there is ambiguity in decryption by the recipient, because after inverting the Vigenère step the digits 211 could be read as either 2 11 or 21 1. More seriously, frequency analysis would be even easier than for standard Vigenère, because in each position (after the permutation step and before the Vigenère step) one would expect 1 to occur by far the most frequently and 2 to occur the second-most frequently.
In the early days of this period, the Viet Minh’s weakness in cryptography resulted to the disclosure of a large amount of confidential information to the French. During the France-Vietnam Conference takes place in Fontainebleau, France from July until August 1946 (when the two sides failed to reach agreement peace treaty), the French were able to read some weakly encrypted Vietnamese diplomatic messages.
Reliance on radio communications also carried serious risks. The French had already sent some of their best code breakers to Indochina so they could inform local and metropolitan French leaders what the other side was saying behind closed doors. Vietnamese efforts at modern diplomacy were hampered on the technological front by their lack of sufficient encryption techniques, equipment, or training. This was particularly true at the beginning of the war, when Vietnamese encryption methods and tables were crude, and inexperienced radio operators too often grew frustrated and simply sent their messages un-coded. As a result, the French were able to read much of the DRV[N]’s cable traffic during the Da Lat conference and also, it seems, during the one at Fontainebleau.
However, the Vietnamese were working hard to improve their cryptographic knowledge. They studied the book Eléments de cryptographie by Captain Roger Baudouin, a comprehensive textbook published in Paris in 1939. In 1948 the Viet Minh published a training manual for cryptographers, which was widely used during the French war. Written by Hoang Thanh and titled Foundations of Cryptography, it is currently on display in the Cryptographic Museum in Hanoi.
There is some evidence that the growing cryptographic sophistication of the Viet Minh center did not necessarily extend to their cadres in the field. A fascinating exhibit in the Hanoi Police Museum depicts an action of Viet Minh commandos who blew up the French ship Amyot d’Inville on 27 September 1950, thereby thwarting a major French attack on the Thanh Hoa – Nghe An – Ha Tınh liberated zone of central Vietnam. The exhibit includes the original instruction sheets describing the cryptography they used. The instructions explain how to use a Vigenère cipher with keylength 5. The keyword TINHA is displayed at the top of a table with the shifted alphabets below. A 17-letter sample message is padded with OOO and then divided into four 5-letter blocks and encrypted. The resulting ciphertext is highlighted in a rectangular box. But alas! The first block of the transmitted ciphertext is the keyword! And everything is nicely spaced so as to leave no uncertainty about keyword length. At least they didn’t have any problem of key distribution!
 The keyword TINHA is the first block of ciphertext.
The keyword TINHA is the first block of ciphertext.
But before we laugh at their blatant violation of Kerckhoffs’ principle, we have to acknowledge that their attack on the French was one of the great successes of a secret guerrilla cell during that epoch. Why didn’t their poor use of cryptography lead to discovery and defeat? Perhaps the French never captured any of their communications, so they could have equally well just sent the plaintext. Or perhaps the French did capture something, but were too ignorant of cryptography even to crack a Vigenère cipher when given the key. Most likely both the Vietnamese commandos and the local French enemy were so isolated that they could not benefit from whatever cryptographic knowledge was in the respective command centers.
2.2. The role of the USSR and China.
In any case, according to the history (NSA 2014), just a few months later, in November 1950, the Vietnamese sent their cryptographers to China for six months of training that greatly improved their technical level. For the Vietnamese at this time, the Chinese experience provided a tremendous model of revolutionary struggle; just the year before the Chinese communists had defeated a Western-supported regime in an epic guerrilla war. However, in communications there was an important difference. The Chinese had to first translate or transliterate to a standard alphabet before encryption. But Vietnamese is written in a modified Latin alphabet, and so can be encrypted directly, provided that some alterations are made. As described in “Vietnam: A SIGINT Paradox” (NSA 2007)
Vietnamese cannot be transmitted by using standard international Morse code because of its peculiar letters and use of accent marks. The [NSA] cryptolinguists had to learn the system created by the Vietnamese to express these features in Morse before tackling an actual translation. For instance, the vowels u and o appear as simple letters or with hooks. To indicate the use of the letter u with a hook, the Vietnamese operator sent the letters uw. W does not exist in the Vietnamese alphabet so it was available for special assignment.
The article goes on to say that because ươ occurs so often, the Vietnamese Morse code operators would shorten uwow to simply wow. … By the beginning of the American war, U.S. cryptographers had a high estimation of the cryptographic level of their adversaries. The declassified history (NSA 2007) concludes, “In 1961…NSA analysts knew that our opponents were good at the cryptologic trade and maintained a healthy respect for the cryptologic abilities of the North Vietnamese.”
2.3. French cryptography in Vietnam (1945–1954)
Like the Viet Minh’s cryptography, the French systems were essentially variants of the Vigenère cipher. In the early years of the war French secret communications were often captured and decrypted (if, in fact, they had been encrypted at all), but by the end of the war their communications security had improved.
The irony is that Blaise de Vigenère was a Frenchman who in the 16th century made major advances in cryptography. At first glance it would seem that the French had made no progress in that field in 400 years. But their real problem was that theoretical knowledge would not carry over to practice, at least not in Vietnam, for three reasons. First of all, in the mid-20th century Vietnam was a remote outpost in the French empire. Hanoi was very far from Paris in every conceivable sense. Moreover, although early in the war France did send some well-trained cryptanalysts to break Vietnamese diplomatic communications, for the most part it was not France’s most intelligent citizens who were sent to Vietnam to combat the independence movement.
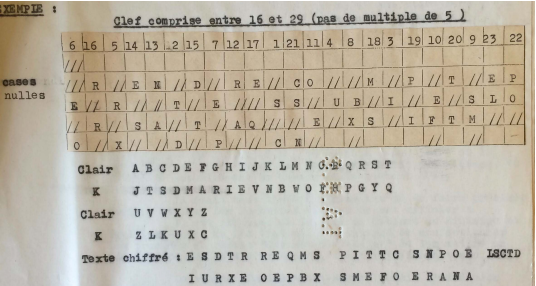 A French military document describes how to encode.
A French military document describes how to encode.
In the second place, in the years before the computer strong encryption was very slow. A document from the military archives dated 7 December 1953 — just three months before the Battle of Dien Bien Phu — reported on an experiment comparing the time needed to encrypt a message using six different encryption schemes. The slowest took 44 minutes, and the fastest took 17 minutes. The conclusion was that the fastest encryption scheme should be used. Note that the recommendation was based on a comparison of speed, not a comparison of security. In the third place, human error and reluctance to follow the rules bedeviled the French authorities. A document dated 11 December 1953 (General Babet’s End of Mission Report, Centre historique des archives) complains about “indiscrétions” and “fautes graves contre ces regles” that had led, among other things, to a recent “coup de main” by the Viet Minh.
The French military commanders acknowledged that in general the most they could hope for was to get their officers to use a very weak encryption. They even introduced a term for that, camoufl´e (“camouflaged”), meaning halfway between plaintext and ciphertext. True encryption was used only for short, top secret documents.
